Federating users using AWS Microsoft AD and on-premise credentials
Federating users using AWS Microsoft AD and on-premise credentials
Federation in AWS
Federation helps to access AWS centrally. Federation helps the credentials from our corporate directory to access AWS accounts using a single sign-on (SSO) mechanism.
To exchange identity and security information between an identity provider (IDP) and an application federation uses open standards, such as Security Assertion Markup Language 2.0 (SAML).
It provides various options for federating our users in the AWS Cloud. We can enable users to sign in to their AWS accounts using AWS Identity and Access Management (IAM) with their existing corporate credentials. When we add more AWS accounts, we can use a single sign-on to manage business applications centrally. We can also add federation to support web and mobile application using Amazon Cognito.
Here we will discuss on federation with AWS Microsoft AD to enable our corporate directory users to sign in to the AWS Management Console with their user credentials to access and manage AWS resources through IAM roles.
Benefits of federating users
- Our users need to remember only one identity for signing in.
- When you remove a user from the corporate directory. AWS Microsoft AD and IAM automatically revoke their access to AWS resources.
- IAM roles provide a convenient way to define permissions to manage AWS resources. By using a trust between AWS Microsoft AD and corporate active directory, we can assign on-premises users IAM roles.
Federation overview
A company wants to enable corporate directory credentials to access AWS Management console. It has two teams (analytics, integration) with different responsibilities for accessing EC2, Redshift and S3. Alice is a member of analytics and bob is a member of integration. The diagram below illustrates the relationship between the corporate active directory and AWS services and roles.
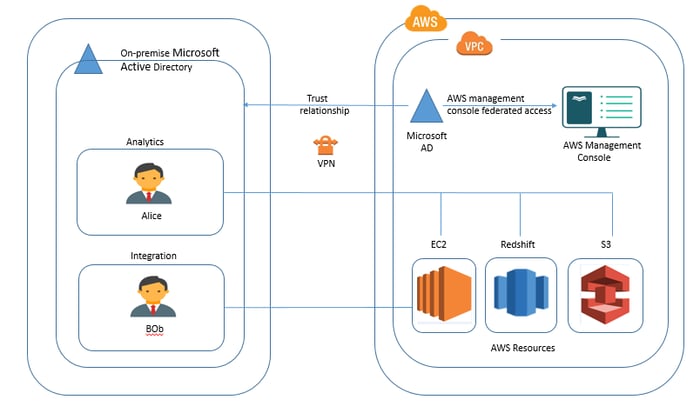
This can be accomplished by the following steps
1. Create an Active Directory in AWS.
2. Create an access URL from an active Directory in AWS.
3. Enable AWS Management Console access.
4. Assign on-premises users and groups to IAM roles.
5. Connect to the AWS Management Console.
Create an Active Directory
The first step is to create an Active Directory. It creates two domain controllers and adds the DNS service.
Create an access URL
To enable access to the management console we have to create a unique access URL for our Microsoft AD Directory. The Access URL does not provide any other access to our directory.
Enable AWS Management Console access
To allow users to sign in to AWS Management Console with their on-premises credentials, we must enable AWS Management Console access for our AWS Microsoft AD directory.
Assign on-premises users and groups to IAM roles
Before accessing the URL. We have to assign corporate users or groups to IAM roles. It restricts which AWS resource can be used by our on-premise users or group from AWS console.
Connect to the AWS Management Console
We can use the URL that is created in step 2 to access the management console. Now users can sign in to the AWS Management Console.
Concise
AWS Microsoft Active Directory makes it easier to connect to the AWS console by using our Corporate Directory, Also it allows you to reuse corporate policies while still controlling access to AWS Resources.