Better Security with Oracle Cloud
Better Security with Oracle Cloud
Security is the protection of Application, Database and Infrastructure from various external attacks and security threats. Security in the cloud is managed across all the three levels (Saas, Paas and Iaas) models. Security concerns associated with in the cloud fall into two broad categories: security issues faced by cloud providers and security issues faced by the customers.
Shared Security Responsibility Model:
Customers to securely run their workloads in Oracle Cloud Infrastructure, they must be aware of their security and compliance responsibilities, security in cloud is a shared responsibility between the customer and oracle.
In a shared multi-tenant compute environment, Oracle is responsible for securing the underlying cloud infrastructure (such as data-centre facilities and hardware and software systems) and customers are responsible for securing their workloads and configuring the services (such as compute, network, storage, and database) securely.
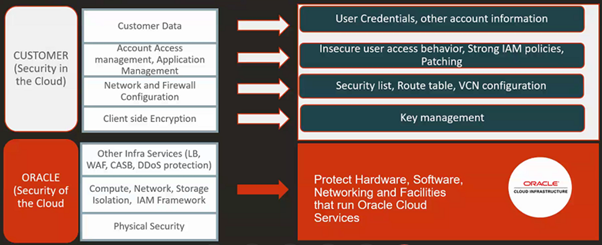
We have the customer and Oracle responsibilities can be divided into the following areas
- Security of the Cloud ( ORACLE)
- Security in the Cloud (CUSTOMER)
Physical Security:
Oracle has the responsibility of protecting the global infrastructure (such as hardware, software and networking) and facilities that run Oracle Cloud Infrastructure services.
Network Security:
Customers are responsible for securely configuring their own Network elements such as VNC, Load-Balancers, DNS and Gateways. Oracle has the responsibility of providing a secure network infrastructure.
Workload Security:
Customer is responsible for protecting and securing their operating system, application layers (patching) and malware attacks. Oracle has responsibility of providing secure images that are hardened and have the latest patches. Also, Oracle makes it simple for customers to bring their own third-party security solutions that they use.
IAM (Identity and Access Management):
Customers are responsible for managing and reviewing access for their own accounts and for all activities that occur under their tenancy. Oracle has responsibility of providing effective IAM services such as identity management, authentication, authorization, and auditing.
Host Infrastructure Security:
Customers are responsible for configuring and managing their compute (virtual hosts, containers), storage (object, local storage, block volumes), and platform (database configuration) services. Oracle shares a responsibility with customers to ensure that the service is optimally configured and secured.
Client and end-point protection:
Customers uses mobile devices and browsers, to access their cloud resources and they are responsible for securing all clients and endpoints on OCI.
Data Classification and Compliance:
Customers are responsible for correctly classifying and labelling their data and meeting any compliance obligations and they are also responsible for auditing their solutions to ensure that they meet their compliance obligations.
7 pillars of Trusted Enterprise Cloud Platform
Oracle has its security approach based on 7 core pillars and each pillar has a multiple solutions to provide a good security and compliance to the cloud platform.
Here are the seven core pillars of trusted enterprise cloud platform:
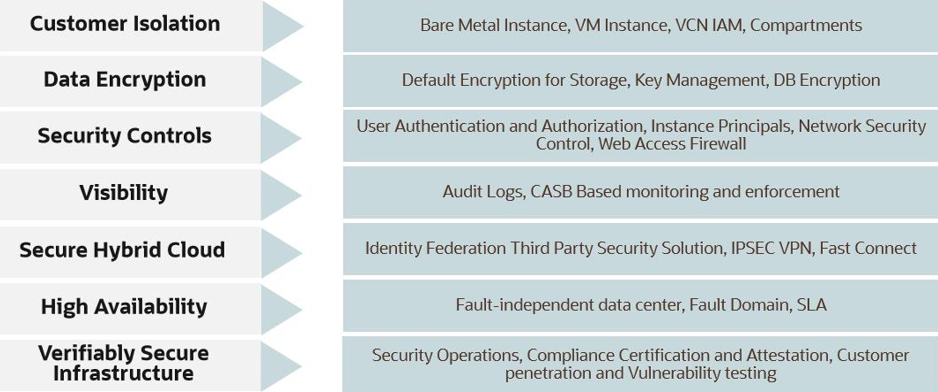
Customer isolation
It allows customers to deploy application and data assets in an environment that commits full isolation from other tenants and Oracle’s staff and also isolate different departments.
Isolation can be achieved by the below components
- Compute (Bare Metal Instance and Virtual Machine Instance)
- Networking (VCN and Subnet)
- IAM (Compartments and IAM Policies)
Data Encryption
Data encryption protects customer data at-rest and in-transit in a way that allows customers to meet security and compliance requirements with respect to cryptographic algorithms and key management.
Below are various encryption strategies:
- Block Volume Encryption
- Object Storage Encryption
- Key Management Service
- Load Balancer
Security Control
Using security control users have access to control the services and segregate the operational responsibilities to reduce the accidental user actions and malicious activities. They also have capabilities to rotate their own credentials and reset those using tenancy security administrator.
Services that have security control are:
- IAM
- Security Lists
- WAF
Visibility
Audit service records all API calls to resources in a customer’s account and also a login activity from the management console. Using the Audit service, customers can achieve their own security and compliance goals by monitoring all user activity within their own tenancy. CASB provides threat detection, predictive analysis and security configuration management of your cloud resources.
Secure Hybrid Cloud
We have different users are capable of accessing the resources in the oracle cloud using the Oracle Identity Cloud Service (IDCS) in which the users are registered with various identity providers like Microsoft Active Directory Federation Service (ADFS) and it uses SAML 2.0 federation for secure identity.
High Availability
In order to reduce the data loss and to secure the data from the unexpected hardware failures and maintenance updates on the computer hardware, a Fault (FD) architecture must be used for provisioning of instances. FD provides high availability for applications which are placed across the different availability domain than that of in the same domain.
Verifiably Secure Infrastructure
Oracle provides compliance, third party audit and certifications and attestations across the different countries in the world and also their associated supported services.
Some of the certificates are:
- ISO 27001
- SOC1,SOC2 and SOC3
- PCI DSS Attestation of Compliance
- HIPAA Attestation
